Share
Forta Firewall Expands Scam Coverage with Address Poisoning
February 5, 2026
•

Address poisoning is deceptively simple and brutally effective. One of the highest-volume scams because it exploits normal user workflows: copying a recipient from transaction history, reusing prior addresses and trusting familiar-looking token names. Firewall is adding Address Poisoning to the list of scam types it monitors and blocks, alongside Phishing Drainers and Fake Token deployments, so chains and applications can stop these threats before funds are lost.
Address Poisoning
Forta Firewall’s Address Poisoning detection is built to catch both the setup and the payoff. And it’s designed for the exact pattern seen in recent high-impact cases, like the ~$50M USDT address-poisoning theft where a victim first sent a test transaction and then got “mirrored” with a zero-value transfer plus a small lure payment, leading to the final mistaken send.
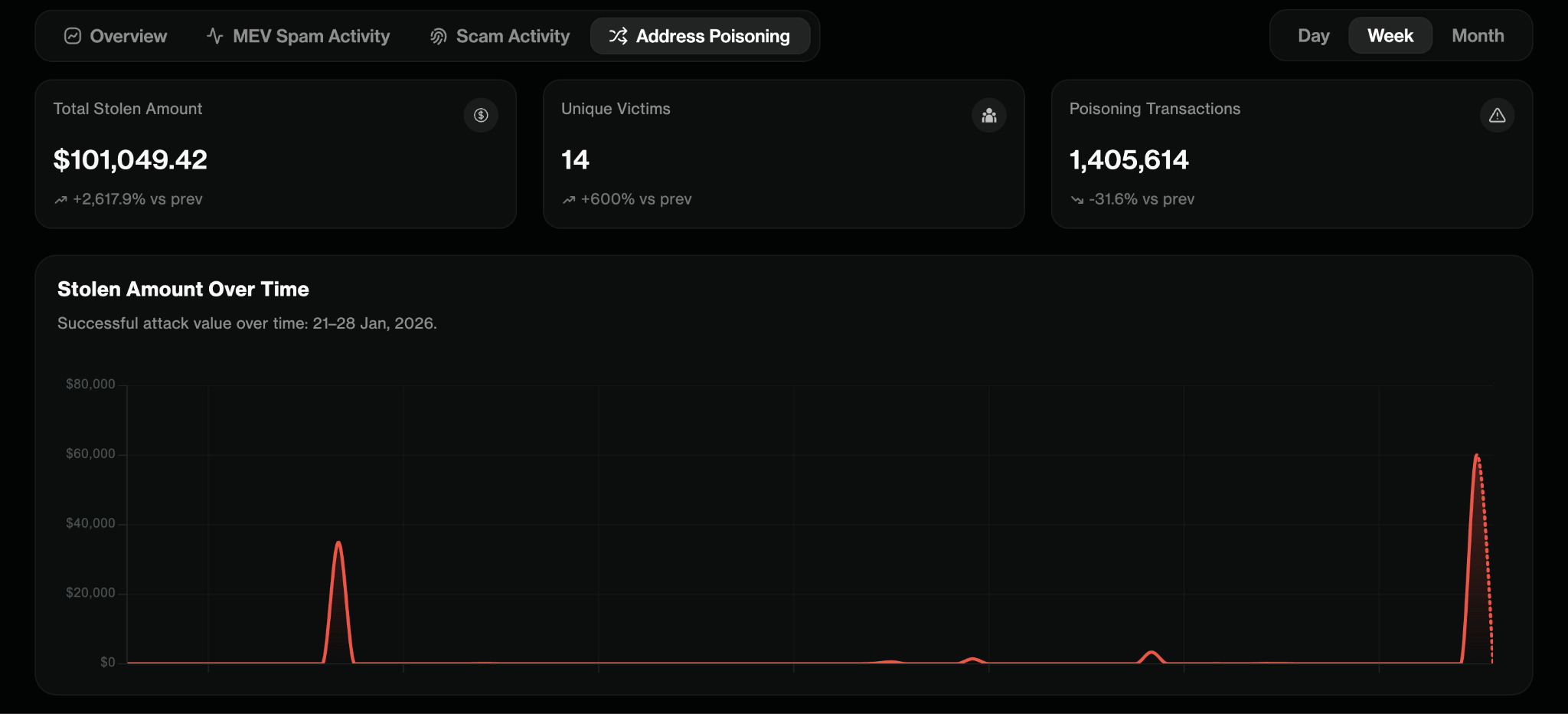
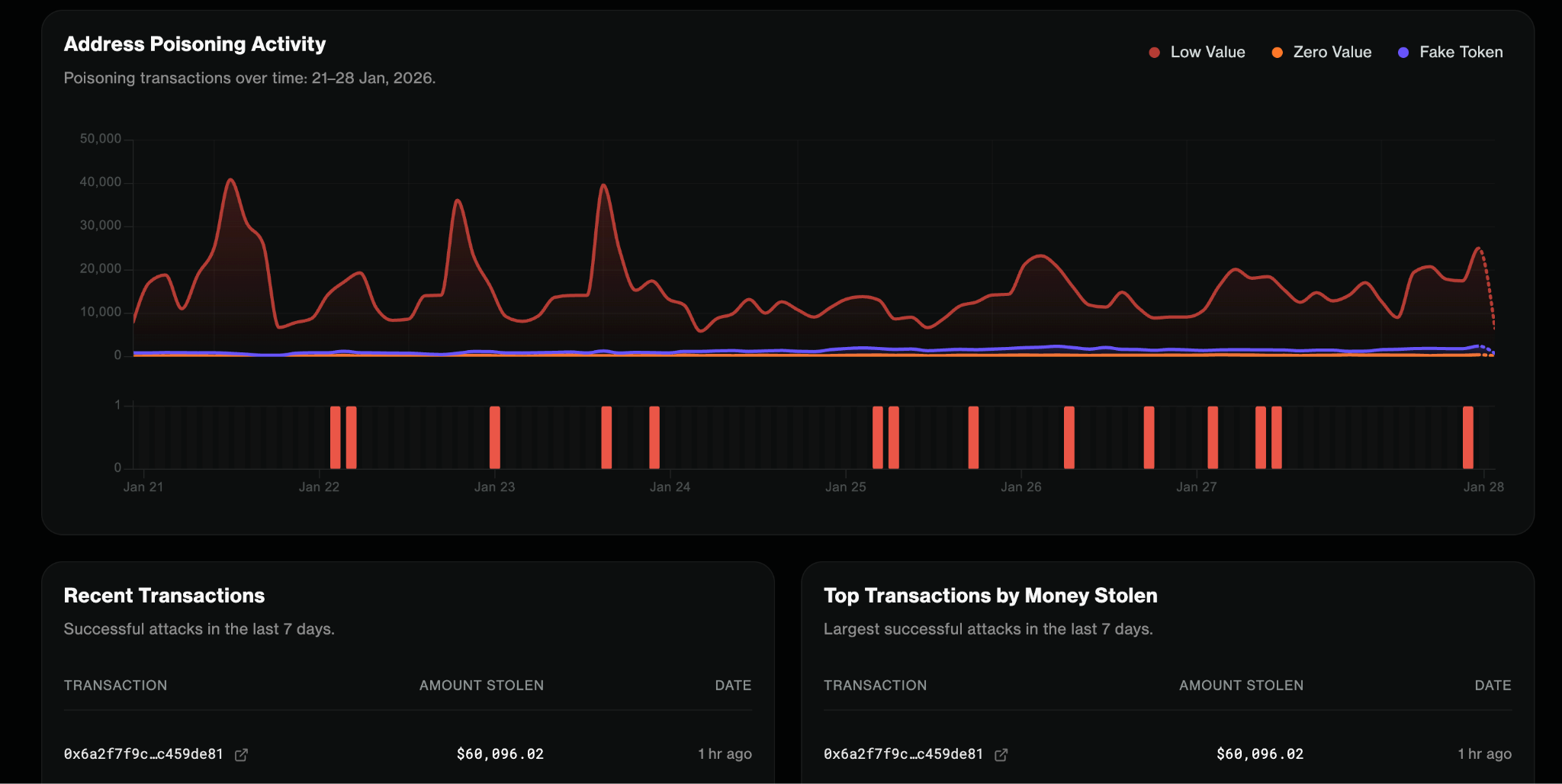
The Address Poisoning module operates in two stages. Distribution Detection identifies when an attacker is poisoning a victim through zero-value transfers, low-value transfers, or fake token transfers. When that behavior is detected, Firewall stores the attacker–victim pair and generates an alert, creating a “watch list” for the next stage.
Success Detection then monitors transactions that involve transfers and cross-references recipients against the stored attacker–victim pairs. If a match is found, Firewall triggers an alert indicating a theft attempt.
Phishing and Drainers
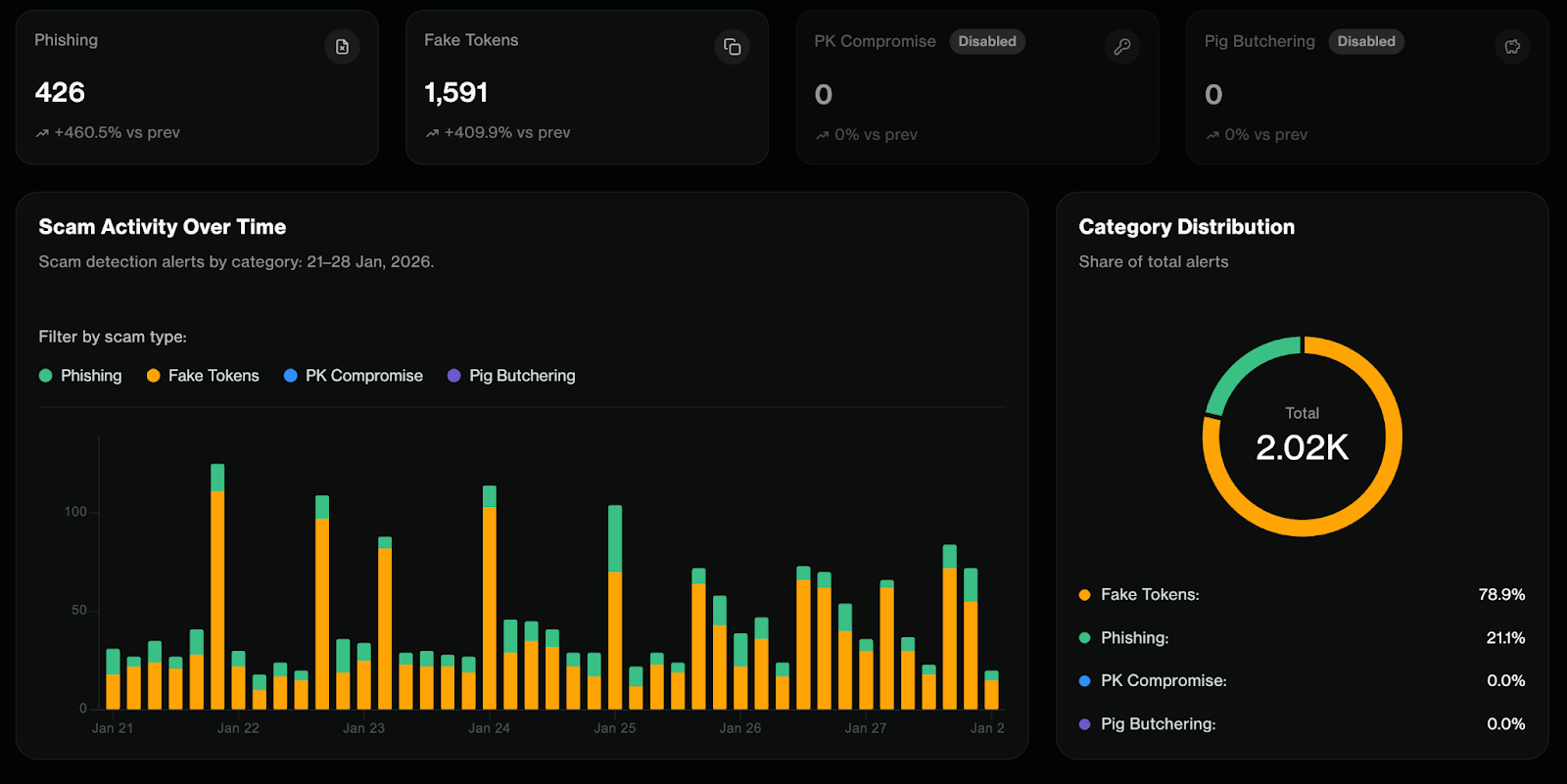
Forta Firewall’s Phishing module focuses on the infrastructure behind wallet draining: drainer kits. These are ready-made deployments sold by vendors that drain wallets once users sign deceiving transactions.
At scale, phishing remains one of the biggest sources of losses on-chain: in January alone, Firewall identified thousands of phishing contracts, giving ecosystems the ability to detect and stop drainer infrastructure before it reaches users.
When Firewall detects a phishing contract deployment, it can flag the transaction or stop it, depending on the chain’s implementation. It can also add the associated contract to a freeze list. This prevents further phishing activity by blocking interactions with flagged contracts and addresses, effectively neutralizing drainer kits and their operators before they can continue harming users.
Fake Tokens
Fake tokens are malicious contracts deployed to mimic trusted tokens by matching name, symbol, and decimals so that users or tools confuse them with legitimate assets. They’re commonly used to enable address poisoning at scale by sending familiar-looking tokens into victims’ wallets and activity feeds, often nudging victims toward malicious links or swap interfaces. Stablecoins and native assets like USDC, USDT, and ETH are frequently imitated due to their ubiquity and perceived safety. In the last 30 days alone, Forta Firewall detected 3,913 fake contracts on Ethereum Mainnet.
Forta Firewall detects these deployments across monitored EVM chains by flagging near name/symbol similarity, identical decimals combined with suspicious deployment patterns, newly deployed tokens with immediate mass transfer behavior, suspicious metadata, and mismatches between on-chain bytecode and expected ERC-20 behavior.
Closing the Loop
Scams today aren’t one-off tricks; they’re pipelines.
By adding Address Poisoning, Forta Firewall tightens protection across a wider range of onchain scams and turns high-confidence detection into real prevention at execution time.
