Community Spotlight: This article was guest authored by an anonymous Forta community member and participant in Forta’s Threat Research Initiative (TRi).

Forta is a real-time detection network for security monitoring of blockchain activity. The decentralized Forta Network scans all transactions and block-by-block state changes, leveraging machine learning to detect threats and anomalies on DeFi, NFTs, bridges, governance and other Web3 systems. When an issue is detected, alerts are sent to subscribers of potential risks, which enables them to take action.
Soft rug pulls are a common type of scam in the cryptocurrency space. Unlike hard rug pulls, which involve malicious code or exploits, soft rug pulls are solely social engineering attacks. Scammers create a token and persuade users to buy it, often using hype and false promises of high returns. Once the price of the token has increased sufficiently, the scammer withdraws all the liquidity, leaving the token worthless and the investors at a loss.
In the past, soft rug pulls were relatively easy to identify due to their blatant tactics. However, as the crypto space evolves, so do the techniques employed by scammers. The campaign we’re discussing in this blog post is a prime example of this evolution. The scammer used advanced techniques and significant funds to make the scam less obvious, making it harder for users to spot the danger. This highlights the importance of real-time threat intelligence in assessing the risk associated with a particular address or token.
The Forta Network is the leading source of this type of threat intelligence. It monitors on-chain activity in real-time across seven EVM compatible chains, covering a broad range of scam techniques, including soft rug pulls. The network uses machine learning to identify potential scammers with high precision and recall. Additionally, the Forta community continuously monitors the threat landscape, ensuring that the network’s capabilities evolve alongside the changing tactics of scammers.
The DZOO campaign is a recent example of a sophisticated soft rug pull. The scammer deployed a fake DZOO token just hours before the launch of the real DZOO gaming token. They created a liquidity pool on Uniswap and attracted 20 victims, who collectively lost 4.4313ETH (or 8757.14 USD). The scammer then withdrew all liquidity from Uniswap, leaving the token worthless. The Forta Network identified the scam on the day it was launched, generating timely threat intelligence to protect users.
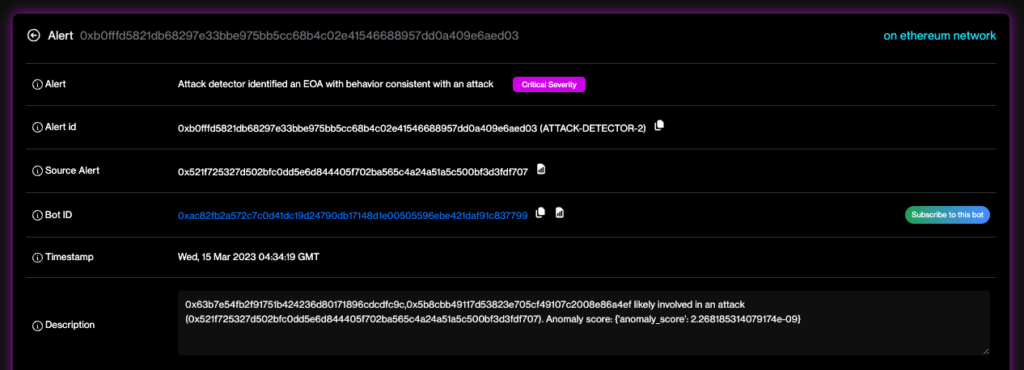
The scammer behind the DZOO campaign, however, used advanced techniques that made the scam harder to spot:
1. The scammer timed the creation of the DZOO token just a few hours before the real DZOO token was created.
2. The scammer utilized significant amounts of funds (at least 724ETH or 1.3M USD) to execute the scam! This illustrates we are dealing with sophisticated groups with significant resources.
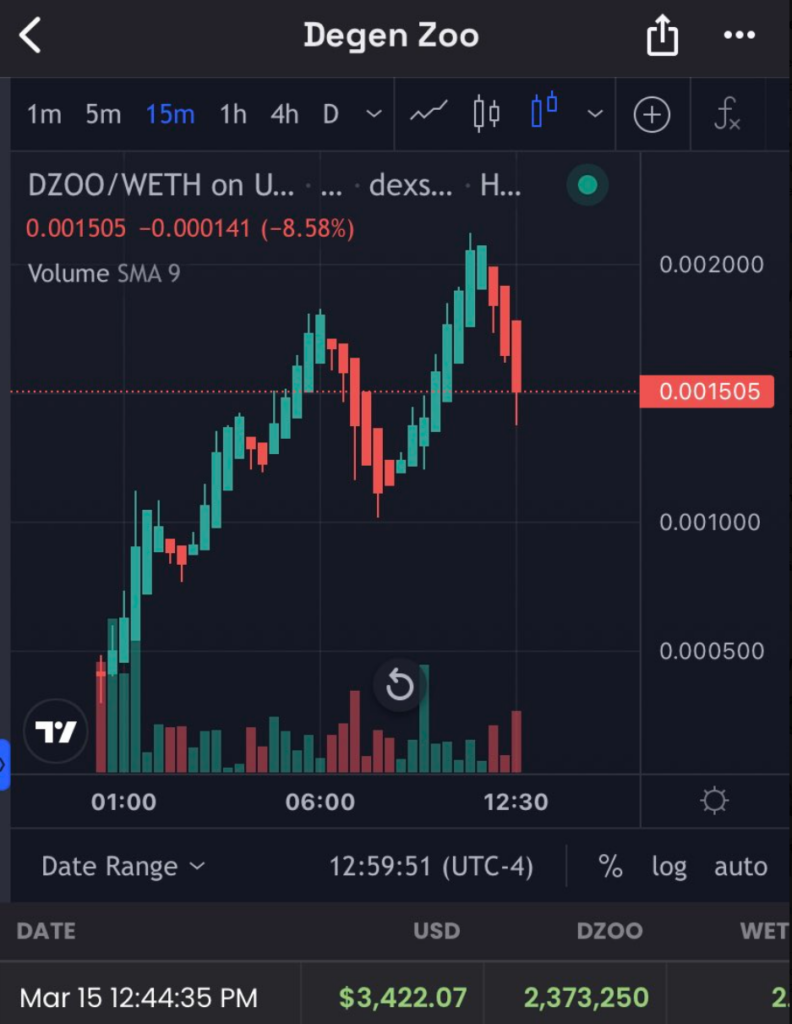
3. Funds were distributed to bot EOAs using the disperse.app to generate trading activity on the created pool resulting in upward price movement:
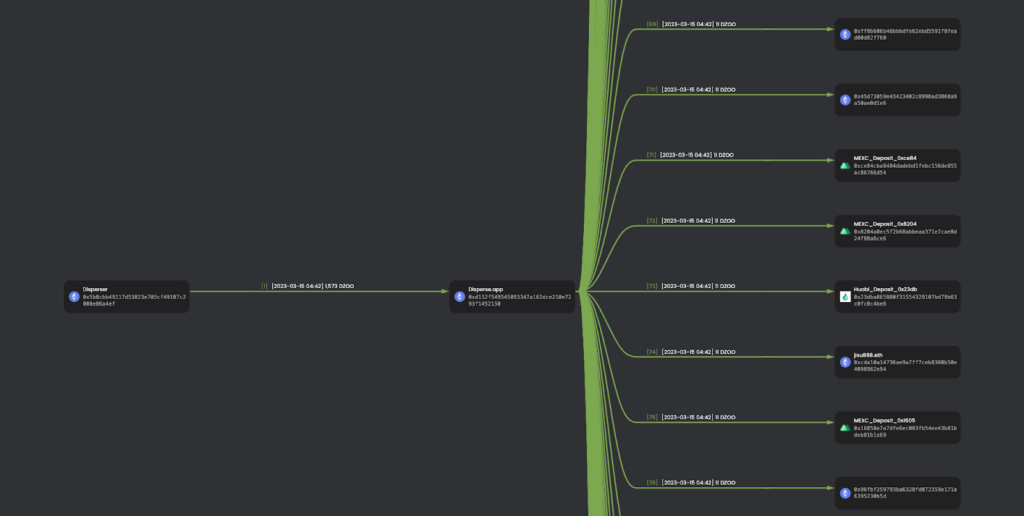
4. The scammer airdropped tokens to a broad range of accounts to inflate the holder count using the disperse.app
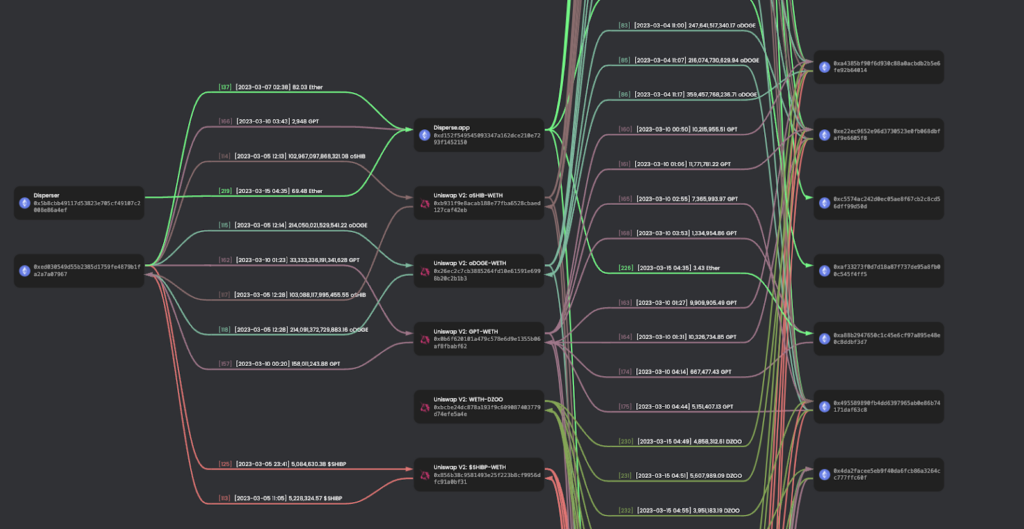
The scammer around DZOO has been active for most of 2023 and has been involved in deployment of several soft rug pull tokens. The technique of utilizing bots to generate trading activity was deployed for several tokens DZOO, oSHIB, oDOGE, GPT, and SHIBP.
To protect oneself from such scams, users should check the Forta Threat Intelligence using before interacting with an unknown EOA/contract. This can be done by personalizing the linked query via Forta Explorer. Alternatively, one can also use a security plugin or wallet, like Blockfence or Zengo wallet, which integrate with Forta Threat Intelligence natively.
Soft rug pulls are a growing threat in the crypto space. As scammers become more sophisticated, it’s becoming harder for users to spot these scams. Access to real-time threat intelligence, like that provided by the Forta Network, is crucial for users to protect themselves.
Appendix 1: Campaign Visualization March 2023
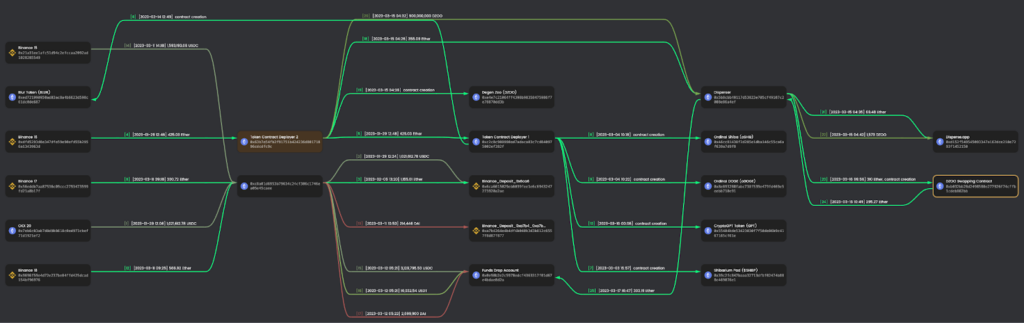
Appendix 2: DZOO Owned Scammer EOAs
0x63B7E54fb2f91751B424236D80171896cDcDfC9c
0x5b8cbb49117d53823e705cf49107c2008e86a4ef
0x0e90b2e2c5978edcf4363317f01d67e4bdae8d2a
0xc2c8c988998ed7adaca03c7cd840975002ef282f
0xc8a01d6953b79634c24cf306c1746ea05e45caee
Appendix 3: Scammer created contracts
0xc8a01d6953b79634c24cf306c1746ea05e45caee
0xe4e7c21064ff4398b98358475986f7e78870dd3b
0x55404bde53423030f7f50de86b9c4167165cf61e
0x39c2fc847baaa32713dfbf02474b888c469076e1
0x8e893280fabc738f539e479fd469e5eebb710e91
0x46cc81438f2d285e1dba146c55ca6af639a7d9f9
0x0b405f415dd65aa5ffb049333a64a3a09e2acce5
0xce5771ccc0066682eecec1a8ed7d21ad53a363f3
0xc29d7945c617ee9f99d9eaf81d2a5f840e7e7110
0xc5a051b4e77f2d6cfa049fe27ed986f4a5c66ee2
0xc8a1ea674c63eb8062a4115422eaf9e1c85b2db0
0x2d130441ca5ef87dae47259304c5e75976c802af
0xed721990950ad03ac8a4b6623d598c61dc0de687
0x445ec96caa6895d8e5b3918c8cf90e98e7ce3e90
0xf4a75a73195ba0b1751ea5f262a943210924317e
0x709fa2bce74d1922649cce5c7564664b28f5a543
0x0d915cec2b332c5a24bdbe5f484c77523c78beee
0x71450127965635601d3eb2e1bee489562d173048
0x9c5e882821dc9d218e71d900bcc7a7933928923b
0xb22eb5a91c2b1180918fbdb17b8cfef4cc6a15c7
0x68c08a00fce88ceecc4d2ed648150683853dfbf6
0xe68a2c0eef74b5d8d2975bbf7a681226e4d7473c
0xe416f17004152f0cbb99f9e9358d9ffe3adb2f44
0xa89060952228c8d2a0019a0b949e90e2fe0a70ef
0x4c8abc4563c415444d05e7ae432df87ea74ff968
0x21b6ee639fdd971ba7a54d8784232f0fc73f3a72
0x91805b540e74d25dcabbd64311ba5902ddb58db9
0x25be5cac44412eb03a67ab2e1cae1414b7f94737
Appendix 4: Bot addresses to purchase DZOO token
0x47ce5A1517AeA97F04D303955B400c6d51830F67
0x4bB06B6BD5243dB37Af144A1d436D27dFeCDe947
0x2ada1083e5e298b9F89FDe63DB44dE388A914D69
0xE7Fb6d6DF50BcdFCF457764D4c4648f56d45De04
0xA4385bf90F6d930c88a0ACBdb2B5E6FE92B64014
0xE22ec9652E96d3730523E0fb068dbfaf9e6605F8
0xC5574AC242D0Ec05ae8F67CB2c8Cd56dFf99D50D
0x495589890Fb4Dd6397965aB0e86b74171dAf63C8
0x11D4FDD564AE1BF3875761606aD0B3A21aF310c5
0x6f1A5a607Ec25567b99947c3471cDE61F3E848AA
0x7De08ABcf75f08aAF6EeFA239fe479d26597Db4E
0xAf33273F0D7D18a87F737De95a8fb00c545F4fF5
0x31612a75F5d646d82b4100D1578019eEfb698DEE
0x77B3DdB51c776bC11Af0D7240A02fE9e46A03340
0xEB60c48a1aeA8a84d3333962d8Fb6529f2A3eF8a
0xDcbA1D220959402eb1Ad903cb6B50aEfB30B03AE
0xa88B2947650c1c45e6Cf97A895E48E0c8dDbF3D7
0xDF2dcF3C6Bb807116d2aD70d0641d1F504903964
0xC864fCa1E9B3f2Bdd0C8206400F3F6530adCdCA3
0x195Ad1daD0525f906D91319FbB22aB0288a6b879
0xFD80E81Df83f34312d966496EA943Cf57070f0Ea
0xbe231b29968b25bbaCB146F9DEBb5e56B443cE7B
0x96E0e0F11A6f1A2C268990067da6d4e0fA851846
0xEC68A45F709735994E5340a73b74A7F53bd7BD47
0x9DD577A45C4daA73ed2cB993740A9953fCa996d2
0xe3Cd01d3372A917986F118161Abc00a5497eb425
0xdfB92fF48aaFA9D4F4Cc6877B8dF0752E063A323
0x4da2FaceE5eB9F40da6FCB86A3264Cc777fFc60f
0x84B8aECa2dadB97A3a7e2CBA0899FE1e13e6152e
0x8908f93A43000A270F9e4F8cbDe6671cCc21fc26
 Share post
Share post