Phishing campaigns have plagued Web3, the impact of these attacks is devastating to end users and their drained wallets. Today’s safeguards today are inadequate, protections need to follow an in-depth approach protecting end-users at the web and transaction level. Forta can provide the necessary intelligence to be utilized by wallets providers in order to protect end-users at the transaction level. This article features a deep dive into the Multi/TrustPad Airdrop Phishing Campaign case study and exactly how Forta detected the scams.
Forta is a decentralized threat detection monitoring network that secures over $36B of Web3’s TVL. Prominent industry news sites like rekt.news and Block Threat Intelligence Newsletter talk about the large DeFi hacks, but what about the attacks that fly under the radar? While dollar amounts may not be as large as the $624M Ronin bridge attack, these attacks usually lead to user’s entire wallets being drained. Crypto Twitter is full of stories of users getting scammed and phished, the number of these scams is likely to be in the thousands. ChainAnalysis estimated losses to exceed DeFi losses by a factor of four.
In this blog post, the focus is on analyzing the ongoing Multi/TrustPad phishing campaign which began over nine months ago. To recap the two types of phishing attacks:
- Phishing: This is a concept that has been around in Web2 for decades. The attack attempts to steal a user’s confidential information by posing as a legitimate entity and tricking the user into divulging confidential information (e.g. a phisher could set up a site that resembles a bank and asks for usernames and passwords). In Web3, the attackers have simply adapted their techniques, targeting the confidential information that is a user wallet’s private key.
- Ice Phishing: This is a technique where the user is tricked into signing a transaction that gives an attacker control over the user’s tokens without divulging the private key. This is possible for the main token standards (e.g. ERC-20, ERC-721, and ERC-1155) as they implement an approval function that allows a user to delegate authority to a 3rd party (e.g. a DEX) to act on behalf of that user on those tokens.
Ice Phishing Case Study
As the Forta Network grows stronger through community contributions, more and more attacks begin to surface. These new attacks represented the starting point for this investigation: The Ice Phishing Bot 2.0 raised an alert on September 8th 2022 at 17:51:49 GMT that read:
Immediate questions arose: Was this indeed an attack? What is the extent of the associated campaign? How well were/are users protected against this campaign?
As a first step, Etherscan may provide additional clues on whether this is indeed an attack. Reviewing the user’s that granted approvals to this EOA show approvals of 4 tokens: WETH, DAI, USDC, USDT. The peculiar aspect of this is a) that these approvals were all mined in the same block, but were all separate transactions and b) that approvals issued by a user usually follow some sort of second transaction, like making a swap. For the victim account shown below, no such transaction existed. Several additional addresses the Ice Phishing Bot 2.0 alerted on followed the same pattern and can be found in the appendix.
ChainAbuse, a few days later, tied this particular alert to multipad-coin[.]org. This was a site mimicking a generic DeFi front-end that the scammer had set up.
This looked like a legitimate site that allows one to claim airdrop tokens for DOGEKING (a legitimate memecoin released well before the attack). It was implied that one could connect their wallet and claim the airdrop through this site. However, upon clicking the ‘join airdrop’ token, a barrage of metamask signature requests appeared. It is interesting to note that a well known social engineering technique is used here to instill a sense of urgency in the victim and create FOMO (fear-of-missing-out) around claiming the airdrop. In addition to a ticking clock, four metamask prompts were shown: WETH, USDC, USDT, DAI. A user that is not able to understand these signature requests may quickly click sign in order to claim the airdrop, racing against the clock.
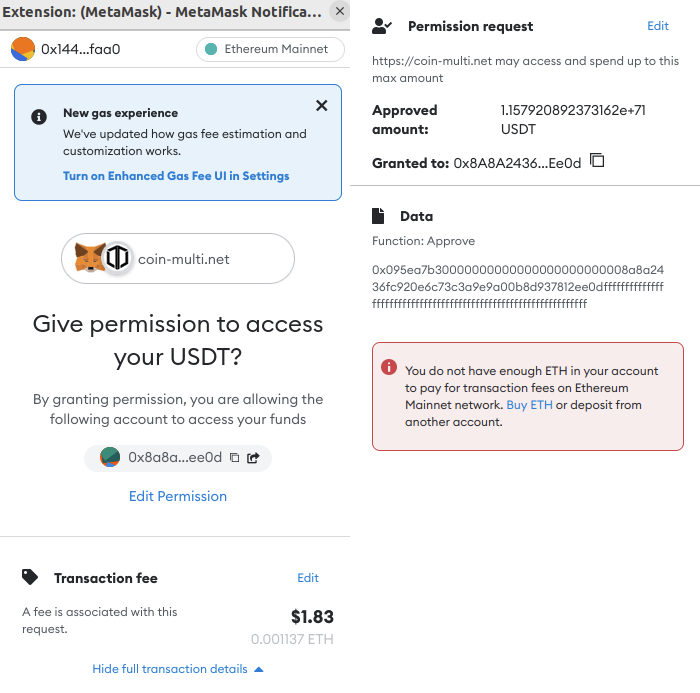
While the above test wallet has no tokens, the user was prompted for WETH, DAI, USDC, and USDT approvals. It is suspected the scammer monitors any deposits and transfers tokens as they get deposited. For users with holdings, the prompts would be customized to their holdings, which the scammer was able to analyze once the wallet was connected to the site.
At this point, the attacker has control of the user’s tokens and transfers them using the transferFrom function to another address that is controlled by the attacker. This happens within a block of the approval transaction, so users who have granted approvals have no chance to revoke approvals to prevent the scam.
The extent of the attack is huge. The scam has lasted over a period of at least nine months involving dozens of web sites (see appendix). There is no connection between the underlying hosting infrastructure or DNS registrar information, but the content follows a similar template with slight customizations.
Interestingly, earlier iterations of the scam actually didn’t perform ice phishing, but rather traditional phishing attack, where the web site asked for mnemonic of the user’s private key demonstrating that attackers continuously tweak their scam to increase ROI.
The attacker drove traffic to their scam through a combination of tweets, YouTube videos, Telegram spam, and comment spam (examples can be found in the appendix). The YouTube videos were not only published by dedicated accounts, but also compromised accounts to leverage existing subscriber bases and translated into different languages indicating the global reach of this campaign.
This is a simple, but effective attack. Over the course of several months, a total of $104K was stolen from 100+ users, excluding funds that may have been stolen due to the phishing attacks (breakdown of stolen tokens in appendix). While this pales in comparison to the large DeFi hacks, it creates tremendous pain for individual users that lose their most valued positions and erodes their trust in Web3. These scams do not necessarily have high conversion rates, but the infrastructure to operate such a scam is likely to be low, and therefore the ROI is tremendously high.
Existing protection against these scams often operate on the URL level. In our tests, the coverage of sites tied to this campaign with URL based protection features was low. This indicates that a protection approach needs to be in-depth that not only protects users from interacting with malicious web sites, but also at the transaction layer. Forta provides intelligence against a broad range of scams: from ice phishing to rug pulls to scam tokens. Each of the addresses associated with this attack was identified by a Forta bot (see appendix). Ask your wallet provider what they do to protect you from such attacks. In many cases, Forta can help.
 Share post
Share post